I prepared this from the requirements so far entered into our confluence page. It is worth noting:
We have no requirements yet where AQ (Accuracy and Quality), IA (Individual access & participation), or PS (Privacy compliance) are the primary considerations. This suggests to me some gaps in our coverage so far.
13 of the 16 requirements apply to verifiers, which aligns with the group’s decision to focus on verifiers first.
Items 7 and 16 appear to be candidates for being merged, but note that the authors identified them with different primary considerations. Worth discussing?
# | Title | Ref | Verifiers | Issuers | Providers | Primary | CC | PL | CL | DM | UR | AQ | OT | IA | AC | IS | PS |
1 | Selective Data Release | 1_BC_CC | FALSE | TRUE | TRUE | CC | Primary | Secondary | Secondary | ||||||||
2 | Encrypted Channel Transactions | 2_ABC_IS | TRUE | TRUE | TRUE | IS | Secondary | Secondary | Primary | ||||||||
3 | Transparency at presentment | 3_C_OT | FALSE | FALSE | TRUE | OT | Secondary | Primary | Secondary | ||||||||
4 | Verifier Identification | 4_A_AC | TRUE | FALSE | FALSE | AC | Secondary | Primary | |||||||||
5 | Inform users of verifier policies | 5_C_PL | FALSE | FALSE | TRUE | PL | Primary | Secondary | |||||||||
6 | Verifiers must attest their use cases | 6_A_UR | TRUE | FALSE | FALSE | UR | Secondary | Primary | Secondary | Secondary | |||||||
7 | Veriferes minimize collection | 7_A_CL | TRUE | FALSE | FALSE | CL | Secondary | Primary | Secondary | Secondary | |||||||
8 | Context for user consent | 8_A_CC | TRUE | FALSE | FALSE | CC | Primary | Secondary | |||||||||
9 | Declare Retention Period | 9_A_UR | TRUE | FALSE | FALSE | UR | Secondary | Primary | |||||||||
10 | Justifialbe PII storage | 10_A_UR | TRUE | FALSE | FALSE | UR | Secondary | Primary | Secondary | ||||||||
11 | Segregated Accountability | 11_A_PL | TRUE | FALSE | FALSE | PL | Primary | Secondary | |||||||||
12 | Secure Storage | 12_A_IS | TRUE | FALSE | FALSE | IS | Primary | ||||||||||
13 | Data Subject Rights | 13_A_OT | TRUE | FALSE | FALSE | OT | Primary | Secondary | |||||||||
14 | Data Registry | 14_A_AC | TRUE | FALSE | FALSE | AC | Primary | Secondary | |||||||||
15 | Separate data | 15_A_DM | TRUE | FALSE | FALSE | DM | Secondary | Secondary | Primary | ||||||||
16 | Verifiers must only request the minimum data required for their transaction | 16_A_DM | TRUE | FALSE | FALSE | DM | Secondary | Primary | Secondary |
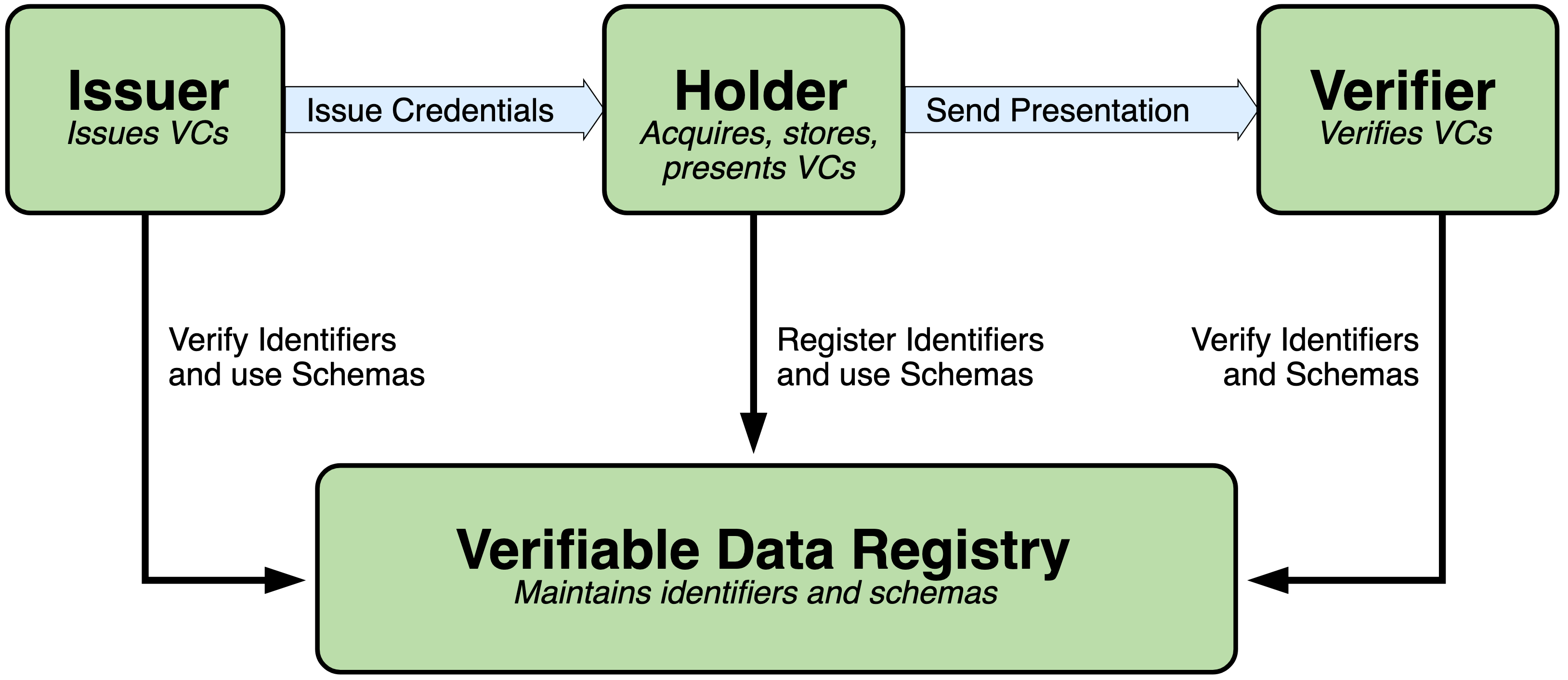
Based on some recent conversations in the workgroup, I’ve updated my thinking on the entities involved in the PEMC ecosystem. We talk about the three endpoints in trusted credentialing systems, using “Issuer,” “Verifier,” and “Holder” or variations of those three in our conversations. This aligns with various versions of the trust triangle that is spoken about in the identity community:
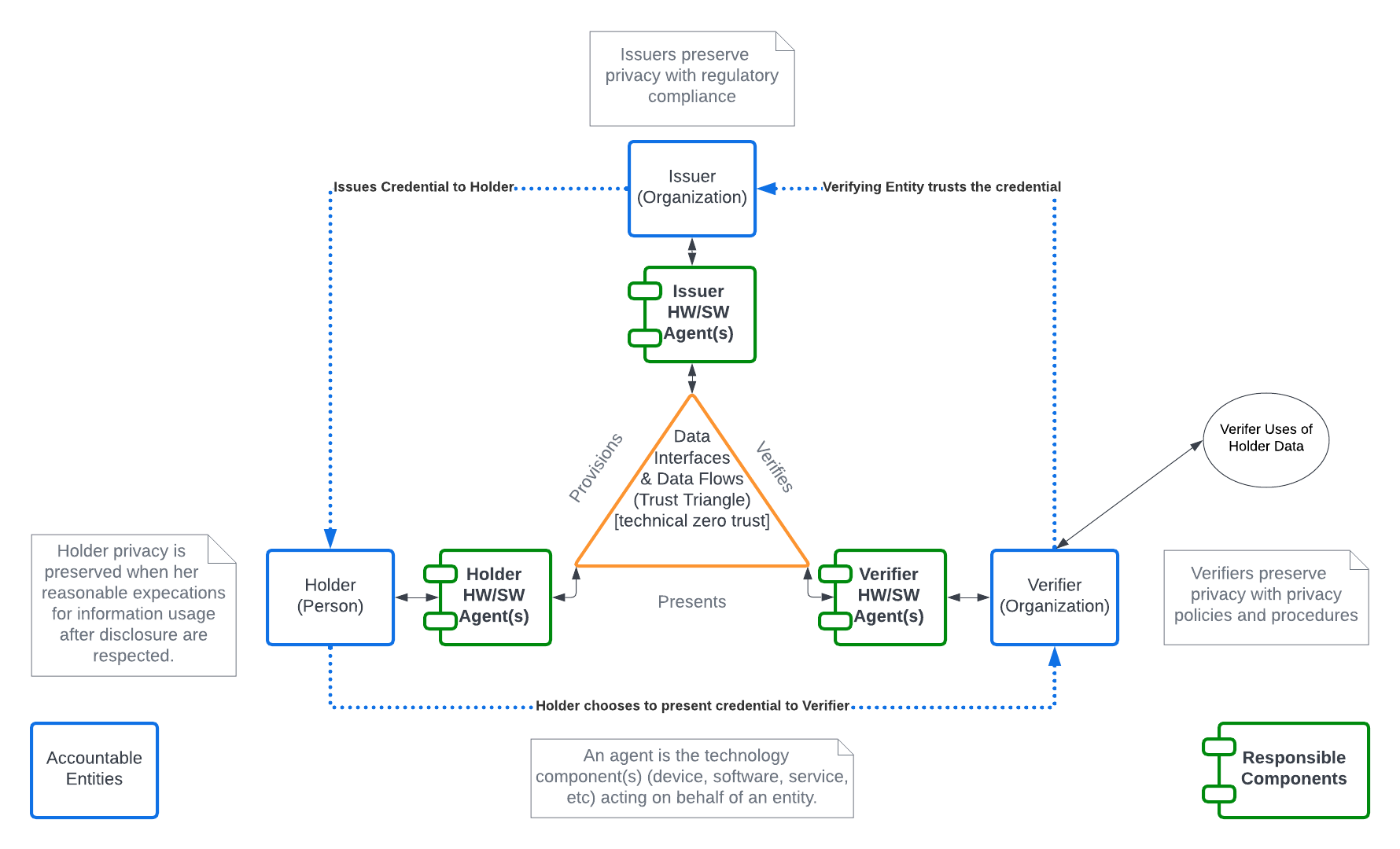
In this workgroup’s discussions about protecting the privacy of individuals and identifying the entities that will be accountable or responsible for meeting requirements for creating and supporting Privacy Enhancing Mobile Credentials, it seems that some roles are being conflated. To that end, I created the following diagram to help me distinguish between the hardware, software, or systems that are the endpoints of the data flows in such a data system and the entities that should use those tools to build trust between themselves. I suggest below that each entity uses an agent, which may be composed of one or more systems for identity.
A Holder Agent would be the combination of mobile devices and apps that contain the Holder’s mobile credential (mDL, Health Card, Student ID, etc.)
A Verifier Agent would be the combination of credential reader and software the Verifiers uses to collect credentials when presented by the Holder.
An Issuer Agent would be the system used by an Issuer to provision a Holder Agent. For the purposes of the PEMC, systems and processes used by the Issuer to collect and verify the information about the Holder are out of scope.
In the diagram below the interior triangle are machine-readable data flows between endpoints. The exterior dotted lines represent the human understandable processes between the entities that use the data flow to accomplish their purposes. This helps me to disentangle, for example, the requirement for a Verifier organization to have policies and training in place for its' staff concerning data collected from a Holder from the requirement of Verifier Agents to implement data minimization in their systems.
Comments are welcome below.