Presentations
Workgroup Presentations
Receipt Presentations from May 24- 2019 -
Sunday.May 24, 2020
AdvCIS Project happy to produce the Kantara 2020 - PrivMas-Eve we had an informal Notice & Consent Call (IPR rules suspended) to talk about some of the latest work awaiting the publication of the ISO 29184 Online Privacy Notices and Consent standard and the start of the ISO Consent Record work, (formerly the Consent Receipt).
In short, this is the Agenda we ended up with for PrivMas.
PrivMas Call Video
PrivMas - Presentation Videos Posted
- Full Video Presentation
- Agenda Cut to
- Welcome to Kantara PrivMas - Colin & Anti-Consentiment - Doc Searls
- The Meaning of PrivMas (Gov-Interop with Social Physics) - Mark Lizar
- A New Governance & EU-Digital Strategy & a Separation of Powers - Mathais De & MyData
- Common Accord - James Hazzard
- AI - Consent Receipt - Alex Demo
- Blinding Identity & ToiP - Making Governance Interoperable - Paul Knowles
- Dynamic Consent(sus) for Emergency Health Responders - Tom Jones
- BRUE: UMA Specific Soup: Demo of Cross Jurisdiction transfers of Electronic Health Exchange Record - Demo
- Special Thanks to vitor jesus (Unlicensed) and Birmingham City University Trust-Less Team
(We were sure to issue a surveillance notice and made sure people knew we were recording.)
Surveillance Notice : The PrivMas call will be recorded, attendee's are invited to change their name and turn off video - and wear a mask to self protect against privacy or security risk
Also, we started working on a new set of common roles - for engineer based role playing for data governance frameworks. Working to update the Alice & Bob Narrative to Consent & Permission.
Kantara - Privacy Demo Day (annual may 24th event)
| Presenter | Title of Presentation | Materials | Notes/Tweets | References |
|---|---|---|---|---|
| Colin Wallis | Kantara PrivMas2020 Special | Video of the PrivMas Call | Colin Wallis (Unlicensed) Kick's off the Kantara PrivMas with international #PrivMas Gifts | Video Link to the Call - is here (its big at the moment) |
| Doc Searls | Anti-Consentiment | The R Button https://cyber.harvard.edu/projectvrm/R-button https://blogs.harvard.edu/vrm/2012/04/15/lets-fix-the-car-rental-business/ | Former user (Deleted) Why #PrivMas needs to kill contract of adhesion - its not human consent | https://www.linuxjournal.com/content/cookies-go-other-way Is the operator the 4th party? http://blogs.harvard.edu/vrm/2009/04/12/vrm-and-the-four-party-system/ |
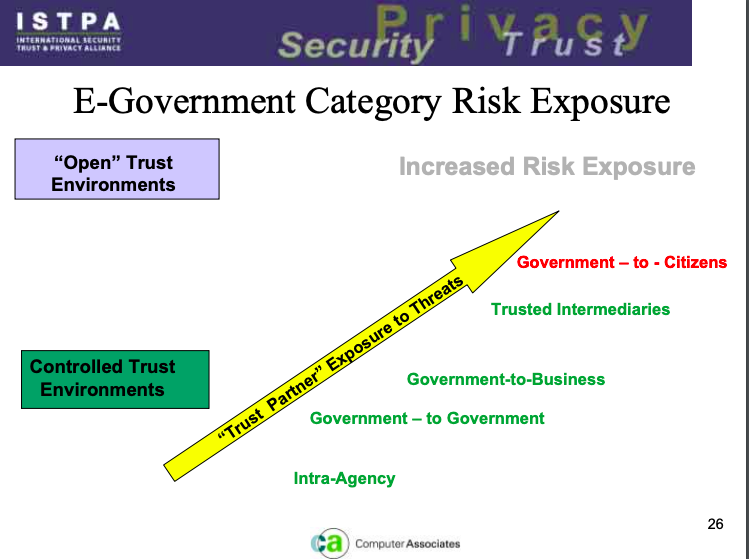
| Mark Lizar | PrivMas -Intro | Review of the history of the legal standards and the background of the work contributed to the OECD Transboarder Flows Guidelines. Referencing 2003 ISTPA - Presentation by John Sabo from OASIS which is very relevant today. In particular slide 26 - Referencing Open Trust environments we are working on in this workgroup today. | Mark Lizar (Unlicensed) #PrivMas History | This presentation.is the 2003 ISTPA Presentation by John Sabo from Computer Associates, which serves a great backgrounder to the legal standards that lead to many of the current technical standards. https://www.oasis-open.org/people/distinguished-contributor/john-sabo |
Mathais De Bievre & Olivier Dion | aNew Governance Project for the EU Data Governance Architecture | European Commission Data Strategy- An infrastructure for decentralised consent (inherent to design) data infrastructure for permissions. Addressing the lock-in of big-data platforms Forming a New Governance in the MyData Community - with interoperability amongst data operator.
| aNG -the upstart EU Network -enjoys PrivMas at Kantara - with Separation of Powers and the Power of Skills & Mobility Use Cases | |
| Joss Langford | MyData Operator |
| MyData Operator - PrivMas at it's best - global best practices | |
| Jim Hazzard | Common Accord | https://hardjono.mit.edu/sites/default/files/documents/CommonAccord_Provenance_11182015.pdf http://www.commonaccord.org/index.php?action=list&file=G/GA4GH/ https://github.com/CommonAccord/Cmacc-Org/tree/master/Doc/G/GA4GH Accountability - e.g. http://www.commonaccord.org/index.php?action=doc&file=G/GA4GH/Accountability-Policy/Form/0.md | Common Accord, a #PriMas gift for a New Governance | |
| Muhammad Waqas | Alexa - AI Consent Receipts | Live Demo of a consent receipt sent via email - where the email must be read before the consent moves from implied consent to explicit consent. Implied to let Alexa offer a service and explicit for access to data - later in the flow - | ||
| Paul Knowles | From the Human Colossus Foundation for scaling data governance -" A home for synergy" | |||
| Tom Jones | A Call To Action for Consent Identity Protocol | Presented a dynamic architecture for real–time emergency response data access, also references to work in Kantara FIRE WG. | ||
| Xiaohu | BRUE: UMA For Cross Domain Explicit Consent (for HealthCare) | I'm hungry. That soup looks awesome! - BlockChain-UMA Specific Soup | ||
| Sal D'Agostino | Identity Surveillance Technology | Bigger Brother -https://www.nybooks.com/articles/2020/04/09/bigger-brother-surveillance-capitalism/ - a SoShanna Zubov Review - And a PrivMas gift - Active transparency Over Surveillance Capitalism | Salvatore D'Agostino Closes #PrivMas Eve - with a Toast and tale of Bigger Brother - to close |
Interop Gov Role-Play For Video Conferencing Calls -
(A use case for facilitating decentralised governance experience - aka consent by design)
This game came about this week as we search for a way to have a Covid PrivMas that was on theme. Realising that some expierencial tools could really help people design with consent and data permissions. To better understand the risks these governance systems have a set of experience driven tools can be developed that helps people experience the surveillance vs consent by design frameworks and permissions that we are designing to replace.
As - how to fix the broken internet game sounded like it could be an idea for future PrivMas fun. Attendee’s participation is (optional) Using video call features people control to turn off video when they want, wear a mask/disguise/sunglasses on the call to make it more comfortable. Be able to come on and off video as person feel's like it, change their screen name to a psudonymn -Basically, turn down the Surveillance to make it more comfortable. etc. is a key first step to trying anything. Which is what we did on the call for PrivMas.
The results below are the raw ingredients.
Objective
The aim of the game is for people to experience what difference governance (Gov) frameworks would be like if implemented the way people think and act. There is a good guy mask, a bad girl mask, a rainbow mask and an imposter mask, for people who don't want to participate in the call, can use the pseudonym Doc or Joyce to participate in a neutral way. The aim is use governance framework names as psudonyms and use the governance frameworks to see if you can work out who is the imposter.
To Participate
Everyone can only invite one guest and you can make up a name for your caller ID (on the video call) by using the suggested identity governance naming convention, that is intended to make transparent the governance framework perspectives you feel like representing on the call or even at different times in the call. (Also, you can exaggerate the name of your favourite governances flavour with a pre-expression to futher exaggerate the naming).
For Example,
ISI Members: as hosts -should pick an ISI Gov flavour name : ISI-N&C Gov, ISI-Intent Gov, etc (as this is prescribed by the role of hosts)
Framework & Protocol Reps: UMA Gov, Skilz Gov, Nxt-ISO-Gov, Me2B Gov, WoT Gov, and interestingly - aNG - doesnt need a naming convention - (these examples are not prescriptive)
Likewise - pls ask your guests to affiliate to whatever Gov label you choose to participate under, e.g. Guest of Gov Name. And for those wishing to be un-afiliated - please name yourself Doc or Joyce to play
Purpose
(More trust and assurance guidance for participation in Gov frameworks to mimick or perform to human expections).This is why we have moderators, and security protocols to kick people out etc, so that the risks can be mitigated
The Game Play Options
The risks mitigated in the call are captured through masking identity in different ways to reduce privacy and security risk of the person, intended to be extremely flexible. Generally, people can identify each other through topic and voice, but the idea is to let people join the call, so no one really knows who each person is to begin with. And with all the video turned off.. as people present, and talk, they can turn on video, and people can communicate via chat.
The call should have one facilitator that can change masks, turning on and off vide.
1 person has to be known and the moderator - another person can be designated the security person for the call. If there is a real (or staged) call disruption - the moderator and the security person has a separation of powers, and need to keep a log of the secret chat where the security person has the decision making power to kick people off the call, but the moderator has the technical control to do so.
Each person's guest can act as a proxy - so their could really be unknown people on the call - which is why its good for a work group/community rather than a public event.
Success
To find the imposter, experience the impact of a governance framework, examine assurances and their integrity specify a governance tool. Explore combinations that are more trust-worthy.
Notes On development
- playing the PrivMas game is needed to develop further and putting in a game play scenario
- For those that play or dev further - pls add update to the comment section below
Videos & Recordings
privmas-01-Doc.mp4privmas-02-aNG.mp4privmas-03-mydata.mp4privmas04-common_accord.mp4privmas05-Alex_receipts.mp4privmas06_Paul_Knowles.mp4 privmas07_TomJones.mp4 privmas08_BRUE.mp4