WG-TFMM Trust as in Trust Framework
Document status: Work in progress
"Trust" as umbrella term
In search of an umbrella term for the frameworks that shall assure information security and privacy the term trust seems to be suitable. It is vague enough to span many concepts, and useless enough to dispensable for specific meanings.
On the other hand "trust" is not useful to convey a specific meaning:
“Trust is a difficult issue to define and contemplate, as it is a human idea with a myriad of general meanings, uses, and associated issues such as risk and privacy. In defining trust many synonyms of trust or trust inspiring terms such as Belief, Credibility, Reliability, Confidence, Faith, Reputation, Competence and Honesty are often quoted.” [Cofta2007]
Guinnane “argues that […] the concept is, at least for economic questions, superfluous: the useful parts of the idea of trust are implicit in older notions of information and the ability to impose sanctions”. [Guinnane2005]. In particular legislation does not rely this term.
Decomposing trust
The purpose of this model is to define a set of specific terms that together are more reliable than a definition of trust.
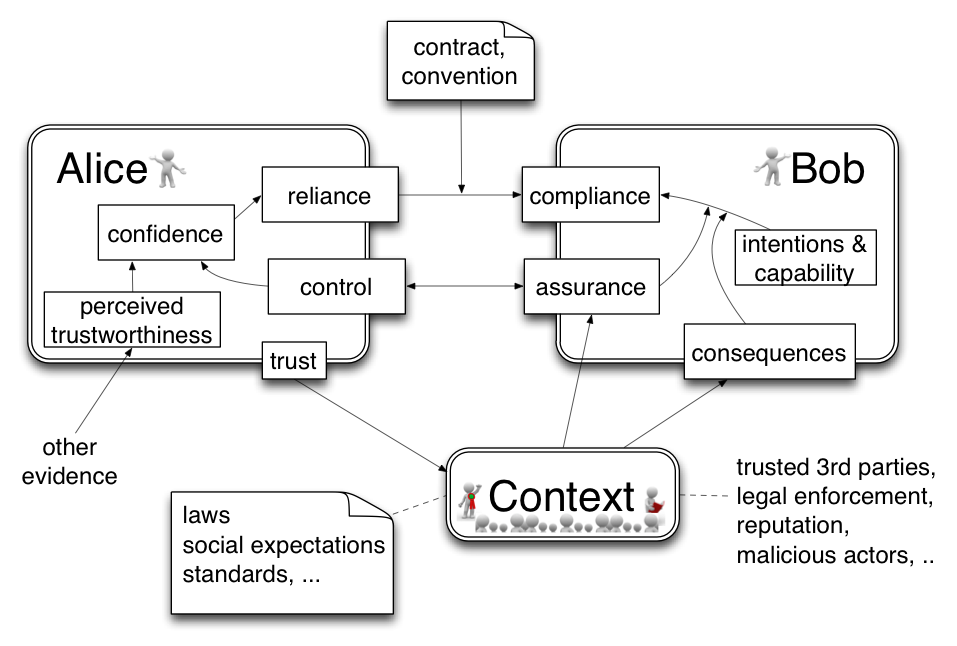
The baseline model: Alice trusts Bob
Alice wants to engage in a transaction with Bob, and has some expectations regarding Bob’s handling of Alice’s risk exposure. Bob acts independently and his intentions may be driven by self-interest or other forces and not be fully aligned with Alice’s expectations. This simple model shows how the behavior of Alice and Bob is driven by internal and external factors:
Alice’s reliance on Bob is driven by her confidence, which might range from low to high. The confidence is an internal assessment based on factual control and perceived trustworthiness, which consists of soft factors like “I always trust properly dressed and polite bank tellers” or “In the Internet I shop only with big global brands”.
Bob’s compliance with laws, standards and contracts is not only based on Bob’s intentions and capability, but also on assurance and the context in form of social expectations and legal enforcement.
Factual control is highly regarded in business environments. Perceived trustworthiness is hard to measure and may evolve over time between actors. At the same time it reduces complexity much more than delegation and control. It is a basic humans skill albeit not very reliable.
Alice’s tradeoffs are:
- Control vs. cost: Too much reliance on control might drive the cost too high to make the transaction feasible, too much required evidence might slow down processes.
- Control vs. complexity: Extensive control requires tightly managed policies and processes that might be infeasible in complex systems.
- Risk vs. opportunity: Setting the risk acceptance low might lead to missing opportunities to delegate, such under-utilizing competent partners with local information
If Alice would be a paranoid control freak, no perceived trustworthiness would be assumed from Bob, even 3rd party root trust would be minimized. In that scenario transactions would be very difficult. At the other extreme, if Alice would relinquish all control, chances are high that some naïve assumptions about Bob’s willingness and competence would be disappointed.
Definitions
Assurance part of a management system focused on providing confidence that requirements will be fulfilled[1|#_ftn1].
Note: In line with the Oxford English Dictionary definition assurance is a declaration and does not imply consequences and enforcement.
Compliance is the behavior conforming to standards, rules and regulations pertaining to the transaction.
Confidence is one’s →believe that other party will willing and competent to behave in a way that is beneficial and desired.
Note: Confidence is internal, not directly visible to an observer, and a unidirectional relationship to the other party.
Control is checking current performance against pre-determined policies, with a view to ensure satisfactory performance[2|#_ftn2].
Perceived trustworthiness is expected behavior in absence of control.
Reliance is the confident behavior towards a trusted party.
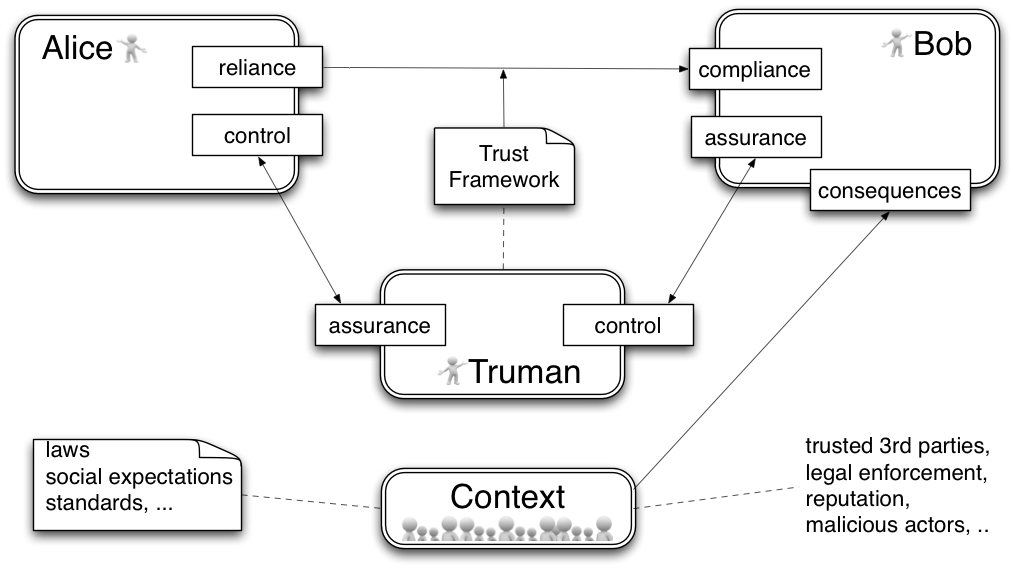
The third party model: Beyond bilateral trust
In contrast to the baseline model that is suitable for 1:1 relationships, Internet-scale federations have to deal with massive amounts of users, a variety of use cases and multiple jurisdictions. Moreover, Bob might be a human, device or network. To conquer this complexity brokered trust is essential. This model also simplifies actors by not trying to have an inner model, but only regard their "interfaces".
Definitions
(these definitions are work in progress!)
Note: Assurance vs. Identity Assurance: Using Identity Assurance would narrow down the scope to the type of frameworks that assure user identity to the SP/RP. To include data protection and attribute assurance the more general term assurance is needed.
Assurance: Processes or deliverables for establishing the information security and data protection requirements of an identified party of a Trust Federation to a degree of confidence that the process or deliverable meets defined by the characteristics or objectives.
Common Operating Rules (COR) set the technical, operation and governance rules for participants in a →Trust Federation.
Trust Federations are a coalition of independent parties to provide protection to electronic communication in a network. For this purpose it legally binds the parties using a multi-lateral contract.
Open issues with this definition: The term Federation has different connotations in the US and Europe. The third party assurance model applies also to centralized cooperation models. (see Cooperation Models for Trust Federations)
Note: The benefit of TFs is to standardize trust relationships so that the setup of individual trust relationships per business case is minimized.
Trust Framework: The combination of a →Legal Framework and →Common Operating Rules that enables parties of a →Trust Federation to rely on other electronically identified parties to fulfill their →Protection Requirements.
Alternative definition: A Trust Framework is developed by a community whose members have similar goals and perspectives. It defines the rights and responsibilities of that community’s participants in the Identity Ecosystem; specifies the policies and standards specific to the community; and defines the community-specific processes and procedures that provide assurance. A trust framework considers the level of risk associated with the transaction types of its participants; for example, for regulated industries, it could incorporate the requirements particular to that industry. See NSTIC Document
Protection requirements in the electronic communication between identified parties are information security, data protection, user autonomy and privacy requirements.
Note: These requirements are for example:
- Assurance of the link of a digital identity credential to a real-world identity (Authenticity)
- Compliance with security objectives for integrity, confidentiality and accountability of the communication
- Adherence to the privacy policy of the PII controller
- Fulfillment of a defined service level (e.g. short- and long-term availability of credentials and services)
- User control over own data (like availability for export in an open format)
Identity Trust Framework
The term Identity in Identity Trust Framework is suggested because most security objectives are to proof identity to a Relying Party. However as mentioned above in “Identity Assurance vs. Assurance” this is too restrictive as it excludes objectives like data protection, privacy and user control.
Therefore I think that Infrastructure Trust Framework or just Trust Framework would be a better term.
References
[Cofta2007] Piotr Cofta. Trust, Complexity and Control: Confidence in a Convergent World. John Wiley & Sons, 2007.
[Guinnane2005] Timothy W. Guinnane. Trust: A Concept Too Many. http://ssrn.com/abstract=680744
[1|#ftnref1] Derived from _Quality Assurance in ISO/IEC 9000:2005
[2|#_ftnref2] Derived from the context of management science. See Wikipedia→Control (management)